Digital Security: Protecting Your Online Presence with Key Products is crucial in today’s interconnected world. From sneaky malware to deceptive phishing scams, the online landscape is full of threats. Ignoring these risks can lead to devastating data breaches and financial losses. This guide explores essential security practices, the best security products, and how to implement them effectively, protecting your sensitive data and maintaining a secure online presence.
This comprehensive guide delves into the intricacies of digital security, offering practical advice and actionable steps to safeguard your online identity and assets. We’ll cover everything from strong passwords and multi-factor authentication to the latest security software and emerging threats. Get ready to navigate the digital world with confidence, knowing you’re armed with the knowledge to stay protected.
Introduction to Digital Security
Source: ftc.gov
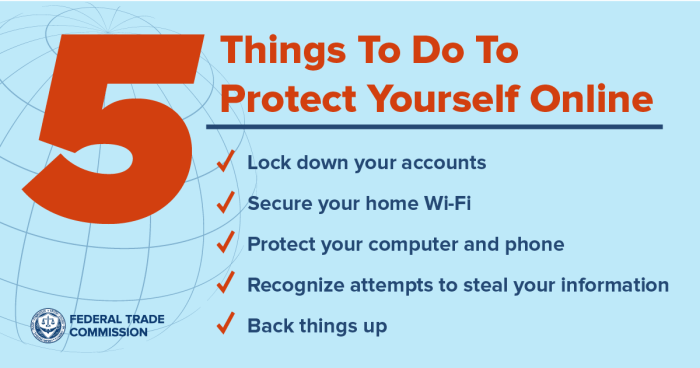
In today’s hyper-connected world, our lives are increasingly intertwined with the digital realm. From online banking to social media, we share sensitive information and engage in countless activities online. This interconnectedness, while offering immense benefits, also exposes us to a multitude of risks. Digital security is paramount in safeguarding our online presence, ensuring the protection of our data and personal well-being. Failing to prioritize it can lead to devastating consequences.
Digital security encompasses a wide range of practices and technologies designed to protect our online activities from malicious actors. It’s about establishing robust defenses against a variety of threats, from insidious malware to sophisticated social engineering tactics. Understanding these threats and implementing appropriate security measures is crucial for navigating the digital landscape safely.
Online Threats
Digital threats manifest in various forms, making it challenging to keep up. Knowing the common dangers is the first step towards safeguarding your online presence. Malware, phishing scams, and social engineering tactics are pervasive examples of these dangers. Malware, in particular, is a broad category of malicious software designed to damage, disrupt, or gain unauthorized access to computer systems.
Potential Consequences of Neglecting Digital Security
The consequences of neglecting digital security can range from frustrating to devastating. Data breaches can expose sensitive personal information, leading to identity theft, financial losses, and emotional distress. Financial losses, ranging from small amounts to substantial sums, can result from various online threats. This highlights the importance of taking proactive steps to protect your digital assets.
Common Digital Security Threats
Protecting your online presence requires understanding the threats you face. Below is a table outlining common digital security threats, their impact, and preventive measures:
| Threat | Description | Impact | Prevention Methods |
|---|---|---|---|
| Malware (e.g., viruses, ransomware) | Malicious software designed to harm or disable a computer system. | Data loss, system damage, financial loss, identity theft. A recent ransomware attack on a major hospital forced them to postpone non-emergency surgeries. | Install robust antivirus software, keep software updated, avoid suspicious downloads, and be cautious of email attachments. |
| Phishing | Deceptive attempts to acquire sensitive information (passwords, credit card details) by masquerading as a trustworthy entity. | Financial loss, identity theft, data breaches. A recent phishing campaign targeting bank customers resulted in several account compromises. | Verify the authenticity of emails and websites, scrutinize links, and avoid clicking on suspicious links or attachments. |
| Social Engineering | Manipulative tactics used to trick individuals into revealing sensitive information or performing actions that compromise security. | Data breaches, financial losses, unauthorized access to accounts. A social engineering attack targeting a company’s employees resulted in the compromise of confidential documents. | Be wary of unsolicited requests for personal information, verify the identity of individuals or organizations, and report suspicious activities. |
| Weak Passwords | Passwords that are easily guessed or cracked. | Unauthorized access to accounts, data breaches, and financial losses. Many data breaches stem from weak or reused passwords. | Use strong, unique passwords for each account, enable two-factor authentication, and consider password managers. |
Essential Security Practices: Digital Security: Protecting Your Online Presence With Key Products
Navigating the digital world demands more than just a cool profile picture and a catchy username. It’s about understanding the crucial steps to safeguard your online presence. This means knowing how to fortify your accounts, protect your personal information, and steer clear of digital traps. Strong passwords, updated software, and a healthy dose of skepticism are your best friends in this digital jungle.
Strong Passwords and Multi-Factor Authentication
Robust passwords are the first line of defense against unauthorized access. Avoid easily guessed combinations like birthdays, pet names, or common phrases. Instead, create unique and complex passwords that incorporate a mix of uppercase and lowercase letters, numbers, and symbols. The longer the password, the better. Think of a password as a digital lock; the more complex the lock, the harder it is to pick. Multi-factor authentication (MFA) adds another layer of security by requiring more than just a password. This could involve a code sent to your phone or an authentication app. MFA significantly increases the difficulty for hackers, making your account much harder to compromise.
Regular Software and Operating System Updates
Software updates are more than just new features; they often include critical security patches. These patches address vulnerabilities that hackers could exploit. Regularly updating your operating system and software applications is a simple yet effective way to keep your digital defenses strong. Imagine your computer as a house; updates are like installing new locks and reinforcing the walls to keep intruders out. Outdated software is an open door for hackers.
Recognizing and Avoiding Phishing Attempts
Phishing attempts are sophisticated scams designed to trick you into revealing sensitive information. These scams often come in the form of deceptive emails, messages, or websites that mimic legitimate services. Be wary of emails requesting personal information, and never click on links in suspicious messages. Verify the authenticity of requests directly with the purported company or service. Think of phishing as a con artist; they prey on your trust, so be vigilant.
Securing Personal Information Online
Protecting your personal information online requires a multifaceted approach. Avoid using the same password for multiple accounts, and enable two-factor authentication wherever possible. Be cautious about the information you share online, and be wary of websites that ask for excessive personal details. Think of your personal information as a valuable treasure; secure it properly.
Password Management Tools Comparison
Choosing the right password management tool can be overwhelming. Here’s a quick comparison to help you decide:
| Tool | Features | Ease of Use |
|---|---|---|
| LastPass | Strong password generation, password syncing across devices, secure vault, and robust two-factor authentication. | Generally considered easy to use, with a user-friendly interface. |
| 1Password | Advanced security features, strong password generation, and secure vault. | Highly regarded for its security and ease of use. |
| Bitwarden | Open-source, free, and highly secure password manager with robust features. | Known for its simplicity and ease of use. |
Note: Ease of use is subjective and can vary based on user experience.
Choosing the Right Security Products

Source: theglobalhues.com
Keeping your digital life safe is crucial, just like choosing the right snacks for a healthy lifestyle. Think about strong passwords and two-factor authentication—essential tools for protecting your online presence. Just like you’d reach for a handful of wholesome nuts or a protein bar instead of sugary treats, prioritize secure practices like those found in top-notch digital security solutions.
For more ideas on smart snack choices, check out our guide on Healthy Snacking: Convenient and Nutritious Options. Ultimately, both your online and physical well-being benefit from proactive choices. So, invest in robust digital security products for a more peaceful online experience.
Navigating the digital security landscape can feel like wading through a murky swamp. There are so many products promising to keep your online life safe, but how do you choose the right one for you? This section dives into the world of security software, helping you understand the different types, their features, and their pros and cons. Armed with this knowledge, you can confidently choose the tools that best protect your digital fortress.
Choosing the right security products is crucial for safeguarding your online presence. A well-chosen combination of tools can effectively defend against various threats, from malware infections to data breaches. Understanding the strengths and weaknesses of different products empowers you to make informed decisions.
Categories of Digital Security Products
Different security products address various aspects of online safety. Knowing the different types and their unique functionalities is essential to selecting the right mix. Antivirus, anti-malware, VPNs, and password managers are common tools that play a crucial role in protecting your online life.
- Antivirus Software: These programs actively scan your computer systems for known viruses and malware, quarantining or removing them before they can cause harm. They typically use signature-based detection, identifying known malicious code, and heuristic analysis to spot suspicious behavior. Think of it like a digital bouncer at the gate of your computer, preventing unwanted intruders.
- Anti-Malware Software: A broader category than antivirus, anti-malware software also targets various forms of malicious software, including spyware, ransomware, and adware, as well as viruses. These programs may utilize more advanced detection methods than basic antivirus software to identify more sophisticated threats.
- Virtual Private Networks (VPNs): VPNs create an encrypted connection between your device and the internet, masking your IP address and protecting your online activity from prying eyes. This is particularly useful when using public Wi-Fi or accessing sensitive data online. They essentially create a secure tunnel for your online traffic.
- Password Managers: These tools securely store and manage your passwords, preventing you from having to remember numerous complex combinations. They often generate strong, unique passwords for different accounts, reducing the risk of account compromise if one password is leaked.
Key Features and Functionalities
Each security product category offers specific features that contribute to its overall effectiveness. Understanding these features helps you choose the best fit for your needs.
- Antivirus and Anti-malware: Key features include real-time scanning, scheduled scans, automatic updates, and the ability to quarantine or remove threats. Advanced features might include behavior monitoring and cloud-based threat detection.
- VPNs: Key features include encryption protocols (like OpenVPN or WireGuard), a wide range of server locations, and kill switches that disconnect your internet connection if the VPN connection drops. Some VPNs also offer additional features like ad blocking or data compression.
- Password Managers: Key features include secure password storage, password generation, automatic filling of login credentials, and syncing across multiple devices. Some tools offer advanced features like two-factor authentication support and the ability to manage other sensitive information like credit card details.
Comparing Benefits and Drawbacks
Different security products have varying strengths and weaknesses. Weighing the benefits and drawbacks is essential for making the right choice.
- Antivirus/Anti-malware: Benefits include protection against known threats, and drawbacks might include occasional false positives and needing to be updated regularly. Consider factors like ease of use, the extent of threat protection, and potential system resource usage.
- VPNs: Benefits include increased privacy and security online, especially on public networks. Drawbacks might include potential speed limitations depending on the VPN server’s location and the need for careful selection of a reputable provider.
- Password Managers: Benefits include enhanced password security and convenience. Drawbacks might include a reliance on the password manager’s security and potential issues if the service is compromised.
Product Comparison Table
Here’s a sample comparison table of various security products. This is fictional data, highlighting the kind of information you should look for when making your choice.
| Product | Price (USD) | Key Features | Customer Reviews (Average) |
|---|---|---|---|
| SecureShield Antivirus | $39.99/year | Real-time scanning, scheduled scans, automatic updates, cloud-based threat detection | 4.5 stars |
| CyberGuard Anti-malware | $29.99/year | Real-time scanning, behavior monitoring, automatic updates | 4.2 stars |
| StealthVPN | $59.99/year | Strong encryption, global server network, kill switch, ad-blocking | 4.7 stars |
| SecureVault Password Manager | $19.99/year | Secure password storage, password generation, automatic login, two-factor authentication | 4.6 stars |
Implementing Security Products Effectively
Level up your online safety game by mastering the practical application of security tools. From installing antivirus software to crafting impenetrable passwords, these techniques are your first line of defense against cyber threats. Don’t just download the software; understand how to use it to its full potential!
Installing and Configuring Security Software
Proper installation and configuration are crucial for security software to function effectively. Incorrect setup can leave your system vulnerable. Begin by downloading the software from a reputable source. Follow the on-screen instructions meticulously, ensuring you agree to the terms and conditions. After installation, configure the software to your needs. Adjust settings to scan for specific threats and set up automatic updates for the latest protection. This proactive approach is essential for staying ahead of evolving cyber threats.
Setting Up and Managing Strong Passwords
Robust passwords are your digital gatekeepers. Weak passwords invite hackers in. Establish a strong password policy for yourself and your organization. Create passwords that are unique, complex, and easily remembered. Avoid using easily guessed information like birthdays or pet names. Utilize a password manager to store and manage your passwords securely. This ensures you have strong, unique passwords for every account, significantly reducing your risk.
Activating Multi-Factor Authentication
Multi-factor authentication (MFA) adds an extra layer of security to your accounts. This is a crucial step to bolster your online defenses. Enable MFA whenever possible to prevent unauthorized access. Typical methods include receiving a code via SMS or authenticator app. This extra verification makes it far harder for hackers to access your accounts, even if they have your password. It’s an essential security measure for personal and organizational accounts.
Updating Software and Operating Systems
Regular software and operating system updates are vital for security. Patches often address vulnerabilities that hackers exploit. Set up automatic updates to ensure your system is always running on the latest, most secure version. This proactive approach is critical for preventing cyberattacks that take advantage of known weaknesses. Outdated systems are significantly more susceptible to attacks.
Creating a Strong Password Policy for an Organization
A robust password policy is essential for organizational security. A well-defined policy can drastically reduce the risk of breaches. Establish clear guidelines for password creation, length, complexity, and expiration dates. Enforce a minimum password length requirement and mandate the use of special characters and numbers. Regularly review and update the policy to keep pace with evolving threats.
| Step | Action |
|---|---|
| 1 | Define password complexity requirements (length, special characters, numbers). |
| 2 | Establish password expiration periods (e.g., 90 days). |
| 3 | Implement a password change notification system. |
| 4 | Implement a password reset policy. |
| 5 | Train employees on the importance of strong passwords and the organization’s password policy. |
Protecting Sensitive Data Online
Staying safe online means understanding the digital threats lurking around every corner. Protecting your sensitive data is crucial in today’s interconnected world. This involves more than just strong passwords; it’s about understanding the various types of data at risk and employing the right security measures. From online transactions to financial accounts, safeguarding your personal information is paramount.
Identifying Vulnerable Sensitive Data, Digital Security: Protecting Your Online Presence with Key Products
Sensitive data encompasses a broad range of personal and financial information. This includes usernames, passwords, credit card numbers, bank account details, social security numbers, medical records, and even location data. Any information that could be used to identify, locate, or compromise your personal well-being or finances falls under this category. The more intricate and personal the information, the more vulnerable it is to cyberattacks. Criminals constantly develop new ways to exploit vulnerabilities, making proactive protection essential.
Securing Sensitive Information During Online Transactions
Online transactions, from shopping to banking, require extra vigilance. Employing secure websites (indicated by “https” in the URL) is a fundamental step. Look for trustworthy websites with verified security certificates. Using strong, unique passwords for each online account further strengthens your security posture. Two-factor authentication adds another layer of protection, demanding an extra verification step beyond your password. Be cautious about clicking on suspicious links or downloading attachments from unknown sources, as these can introduce malware. This vigilance is crucial for safeguarding your sensitive data during online activities.
The Role of Encryption in Protecting Sensitive Data
Encryption is a powerful tool in the fight against online threats. It transforms readable data into an unreadable format, making it inaccessible to unauthorized individuals. Strong encryption algorithms ensure that even if intercepted, the data remains incomprehensible without the decryption key. Think of it as a digital lock and key system for your information. Robust encryption is vital for safeguarding sensitive data transmitted over networks or stored on devices.
Best Practices for Protecting Financial Accounts Online
Protecting financial accounts requires a multi-faceted approach. Regularly monitor your account statements for any unusual activity. Immediately report any suspicious transactions to your financial institution. Enable two-factor authentication for added security. Choose strong, unique passwords for your online banking accounts, different from those used for other online services. Avoid using public Wi-Fi networks for sensitive transactions, as they are often vulnerable to interception. These measures are critical for maintaining the integrity of your financial accounts.
Methods for Encrypting Data
- Symmetric-key encryption uses the same key for encryption and decryption. This method is fast and efficient, but key management is crucial. If the key is compromised, the entire encrypted data is vulnerable.
- Asymmetric-key encryption uses a pair of keys: a public key for encryption and a private key for decryption. This method is more secure regarding key management, but it can be slower than symmetric-key encryption.
- Hashing algorithms generate unique fingerprints of data. They’re primarily used for data integrity verification rather than full encryption, but they’re crucial for detecting data tampering.
These different encryption methods offer varying levels of security and efficiency, each with its own set of advantages and disadvantages. Choosing the appropriate method depends on the specific needs and priorities of the user.
| Encryption Method | Strengths | Weaknesses |
|---|---|---|
| Symmetric-key | Fast, efficient | Key management vulnerability |
| Asymmetric-key | Strong key management | Slower than symmetric-key |
| Hashing | Data integrity verification | Not suitable for full encryption |
Maintaining a Secure Online Presence
Navigating the digital world requires more than just having strong passwords. It’s about proactively safeguarding your online identity and information. This involves a multi-faceted approach, encompassing regular security audits, training, staying informed, and knowing how to react in the event of a breach. It’s like having a personal security system for your digital life.
A strong online presence isn’t just about looking good; it’s about protecting what matters most. Regular security checks, combined with ongoing awareness training, can prevent many potential issues. This proactive approach helps you stay ahead of evolving threats and minimizes the risk of costly data breaches.
Regular Security Audits
Regular security audits are crucial for identifying vulnerabilities in your digital defenses. They involve a thorough examination of your online activities, from the software you use to the websites you visit. These checks help pinpoint potential weaknesses before cybercriminals exploit them. By consistently evaluating your security posture, you can proactively patch holes and strengthen your defenses. Think of it as a preventative maintenance check for your digital life.
Security Awareness Training
Security awareness training equips you with the knowledge and skills to recognize and avoid online threats. This training often involves interactive modules, simulations, and real-world examples that help users understand the latest phishing tactics, malware infections, and social engineering strategies. Regular training sessions empower individuals to make informed decisions and protect themselves from common cyber threats.
Staying Informed About Emerging Threats
Cybercriminals are constantly evolving their tactics. Staying informed about emerging threats is vital for maintaining a secure online presence. This includes following reputable security news sources, subscribing to newsletters from cybersecurity experts, and participating in online communities dedicated to digital safety. By staying abreast of the latest threats, you can proactively adapt your security measures and safeguard your online assets.
Responding to a Suspected Security Breach
A suspected security breach demands a swift and decisive response. Immediately report any suspicious activity, such as unauthorized access attempts or unusual logins. Change your passwords immediately, and contact relevant authorities for guidance and assistance. This proactive response can minimize the impact of a potential breach and help you recover quickly. Timely action is crucial in mitigating the damage.
Security Awareness Training Programs
Regular training is essential for building a secure digital life. It’s crucial to understand the different types of training programs available.
| Training Program Type | Description |
|---|---|
| Phishing Awareness Training | Focuses on recognizing phishing attempts, including emails, messages, and websites designed to trick users into revealing sensitive information. |
| Malware Awareness Training | Teaches users how to identify and avoid malicious software like viruses, spyware, and ransomware. It highlights safe download practices and the importance of updating software. |
| Social Engineering Awareness Training | Covers various social engineering techniques used by cybercriminals to manipulate users into divulging confidential information. It focuses on recognizing manipulation tactics and avoiding traps. |
| Password Management Training | Emphasizes best practices for creating strong and unique passwords, avoiding password reuse, and using a password manager for security. |
| Data Protection Training | Highlights the importance of handling sensitive data securely, including physical and digital protection measures. It covers the importance of data encryption and secure storage practices. |
Case Studies of Successful and Unsuccessful Security Implementations
Navigating the digital world requires more than just a strong password. It demands a deep understanding of how companies protect – or fail to protect – their digital assets. This section dives into real-world examples, highlighting the critical lessons learned from both successes and devastating failures in cybersecurity. These insights are crucial for anyone seeking to safeguard their online presence.
Companies often face immense pressure to balance robust security with a seamless user experience. Poorly implemented security measures can lead to frustrating user experiences, deterring customers and potentially impacting the bottom line. Conversely, well-implemented security protocols can foster trust and confidence.
Successful Security Implementations
Strong security isn’t just about fancy tech; it’s a holistic approach. Companies that successfully implemented robust security measures often prioritized a multi-layered strategy. This approach involves various security layers that complement each other to protect against various threats.
- Strong Password Policies: Companies like Google, with its emphasis on strong, unique passwords and two-factor authentication, have effectively mitigated password-related breaches. These policies drastically reduced the risk of unauthorized access by enforcing complex password requirements and multi-factor authentication, making it harder for attackers to exploit compromised credentials.
- Robust Data Encryption: Financial institutions like banks frequently utilize end-to-end encryption to protect sensitive customer data during transit and storage. This ensures that even if a data breach occurs, the data remains unreadable to unauthorized individuals. This is a critical step in safeguarding user information and maintaining customer trust.
- Proactive Threat Detection: Companies like Microsoft, through its advanced threat intelligence systems, proactively detect and respond to emerging cyber threats. By implementing proactive threat detection systems, companies can identify and address vulnerabilities before attackers can exploit them, reducing the potential for significant damage.
Unsuccessful Security Implementations
Unfortunately, not all companies prioritize security effectively. The consequences of poor security practices can be severe.
- Insufficient Security Awareness Training: Companies that failed to provide adequate security awareness training often experienced breaches related to phishing attacks and social engineering. Employees lacking knowledge about phishing scams and other social engineering tactics are vulnerable to these attacks, compromising company data and confidential information.
- Inadequate Network Security Measures: Some organizations neglected basic network security measures, such as firewalls and intrusion detection systems. This oversight made them susceptible to widespread attacks, potentially leading to the compromise of multiple systems and data loss.
- Failure to Update Software: The failure to patch and update software vulnerabilities can expose companies to severe breaches. Cybercriminals frequently exploit known vulnerabilities in outdated software to gain unauthorized access to systems.
Lessons Learned
Analyzing these examples reveals crucial lessons for any organization.
- Proactive Security is Key: Implementing security measures proactively is essential, rather than reacting to incidents after they occur. A robust security posture involves anticipating potential threats and developing mitigation strategies.
- Multi-Layered Approach: Implementing a multi-layered approach to security is crucial. This includes various security layers, such as firewalls, intrusion detection systems, and security awareness training, to provide comprehensive protection against various cyber threats.
- Regular Security Audits: Regular security audits are vital to identify vulnerabilities and ensure security measures remain effective. This approach ensures that security measures remain effective and can be adapted to new threats.
Impact on User Experience
Effective security measures don’t have to negatively impact the user experience.
- User-Friendly Security Protocols: Robust security measures can be integrated into user interfaces without compromising usability. This is achieved by carefully designing and implementing user-friendly protocols that minimize friction and provide an exceptional experience for users.
- Transparent Security Policies: Clear and transparent security policies help users understand the importance of security measures and encourage compliance. This approach ensures that users understand the reasons behind the security policies, promoting a sense of trust and collaboration.
Case Study: Target Data Breach
The 2013 Target data breach serves as a stark reminder of the potential consequences of inadequate security. Millions of customer credit card and personal details were compromised. This led to significant financial losses for Target and eroded consumer trust. The incident highlighted the critical need for robust data security measures.
Future Trends in Digital Security
The digital world is constantly evolving, and so are the threats lurking within its vast expanse. Staying ahead of the curve in digital security requires a proactive approach, understanding emerging vulnerabilities, and adapting to the ever-changing landscape of technology. The future of security is not just about reacting to attacks, but about anticipating them and implementing preventative measures.
The cybersecurity landscape is shifting rapidly, driven by advancements in technology, user behavior, and the sophistication of cybercriminals. This evolution necessitates a deeper understanding of future trends to ensure a secure online environment for everyone. Predicting the future is inherently challenging, but by analyzing current trends and technological advancements, we can gain valuable insights into what lies ahead.
Emerging Threats and Vulnerabilities
The digital frontier is constantly being tested, and new threats emerge with surprising frequency. These threats aren’t limited to traditional malware; they also include social engineering tactics, vulnerabilities in IoT devices, and attacks exploiting artificial intelligence itself. The rise of ransomware, phishing campaigns targeting specific demographics, and the increasing use of AI-powered attacks are all indicators of a more complex and sophisticated threat landscape. For example, the increasing reliance on interconnected devices creates a vast network of potential entry points for attackers, while AI-powered attacks can be highly targeted and personalized.
Evolution of Security Technologies
Security technologies are constantly evolving to keep pace with these emerging threats. We’re seeing a move towards more proactive and predictive security measures, incorporating machine learning and AI to identify patterns and anomalies. The development of zero-trust architectures, which assume no device or user is inherently trustworthy, is another crucial aspect of this evolution. This trend is particularly relevant given the increased use of cloud computing, where security must be embedded into every layer of the system. For instance, cloud security platforms are being designed to detect and respond to threats in real-time, while zero-trust architectures ensure only authorized users and devices have access to sensitive data.
Artificial Intelligence and Machine Learning in Security
AI and machine learning are revolutionizing security by enabling automated threat detection and response. Algorithms can analyze vast amounts of data to identify suspicious patterns and anomalies, alerting security teams to potential threats before they can cause significant damage. This proactive approach is a game-changer, moving security from a reactive to a predictive model. For example, AI-powered systems can analyze network traffic for unusual patterns, identifying malware or intrusions in real-time. Similarly, machine learning algorithms can be trained to recognize the characteristics of malicious emails or websites, enabling more effective spam filtering and phishing detection.
Innovative Security Solutions
The future of security is not just about preventing attacks; it’s about adapting and evolving to stay ahead of the curve. This includes the use of blockchain technology for secure data management, quantum-resistant cryptography to counter future threats, and the integration of security into the design phase of new technologies. For instance, blockchain can be used to create tamper-proof records of transactions and data, making it more difficult for attackers to alter or manipulate information. Quantum-resistant cryptography is essential to protect data from attacks by future quantum computers. Finally, incorporating security into the design phase ensures that new technologies are secure from the start, mitigating the risk of vulnerabilities being exploited.
Hypothetical Future Security Landscape
A future security landscape focused on prevention will involve a shift from reacting to threats to proactively mitigating them. Imagine a world where security is embedded in every device and application, with AI and machine learning constantly monitoring for anomalies and suspicious activity. Zero-trust architectures will be commonplace, ensuring only authorized users and devices have access to sensitive data. This proactive approach will rely heavily on AI-powered systems that learn from past attacks and adapt to new threats in real-time. The result is a more resilient and secure digital environment for everyone.
Last Recap
In conclusion, safeguarding your digital presence requires a multifaceted approach. By understanding the various threats, adopting robust security practices, and selecting the right security products, you can significantly reduce your vulnerability to online risks. Regular audits, security awareness training, and staying informed about emerging threats are vital components of a proactive security strategy. This guide has provided the tools and insights necessary to build a secure online ecosystem. Stay vigilant, and stay safe online.